One of the most frustrating things about phishing is that most people know what it is and how it works, but many still get caught.
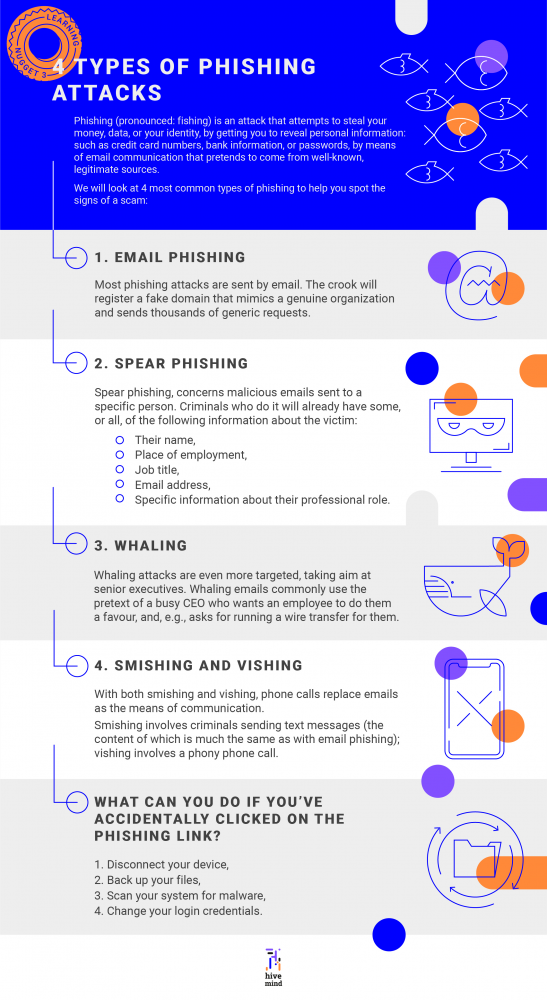
Phishing (pronounced: fishing) is an attack that attempts to steal your money, data, or your identity, by getting you to reveal personal information: such as credit card numbers, bank information, or passwords, by means of email communication that pretends to come from well-known, legitimate sources.
We will look at four most common types of phishing to help you spot the signs of a scam.
1. Email phishing
Most phishing attacks are sent by email. The crook will register a fake domain that mimics a genuine organization and sends thousands of generic requests.
The fake domain often involves character substitution, e.g., using ‘r’ and ‘n’ next to each other to create ‘rn’ instead of ‘m’.
In other cases, the fraudsters create a unique domain that includes the legitimate organization’s name in the URL, as pictured below:
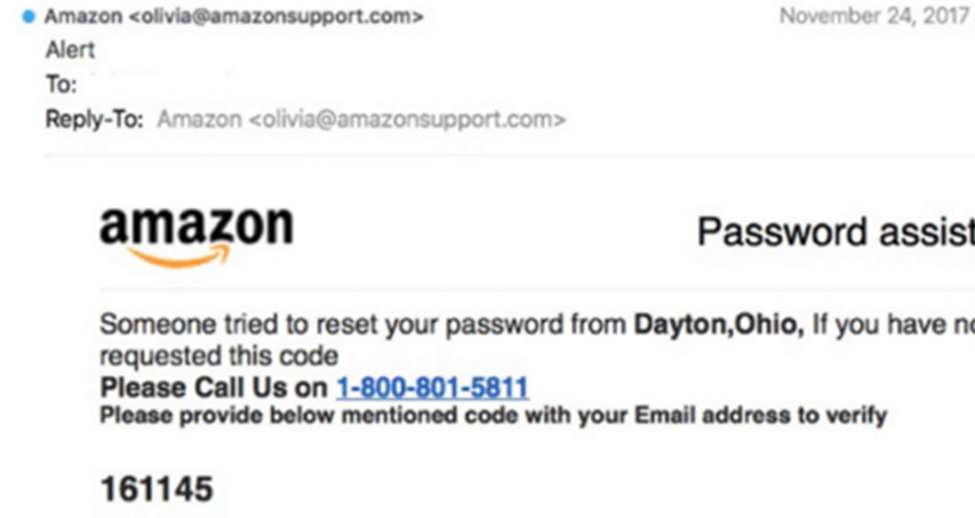
2. Spear phishing
There are two other, more sophisticated, types of phishing involving email.
The first, spear phishing, concerns malicious emails sent to a specific person. Criminals who do it will already have some, or all, of the following information about the victim:
· Their name,
· Place of employment,
· Job title,
· Email address,
· Specific information about their professional role.
Here’s an example of such a scam email:
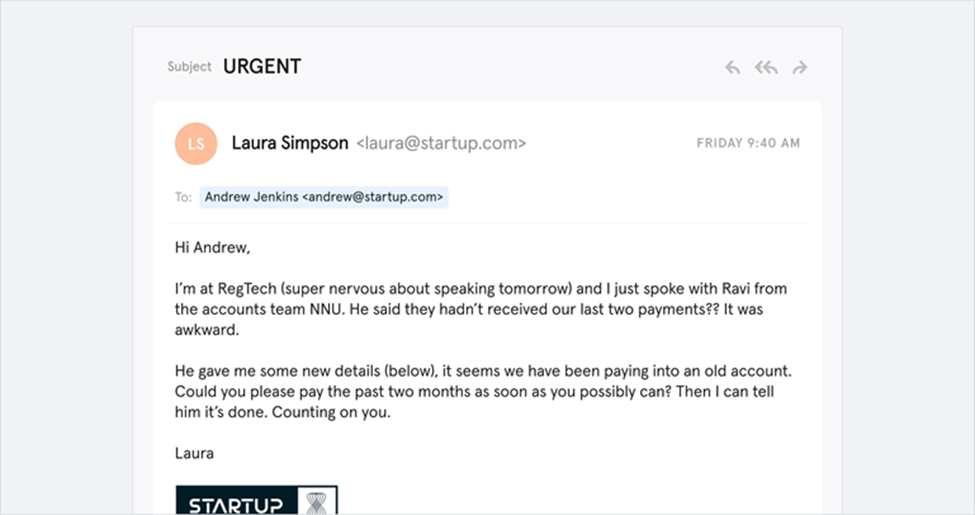
3. Whaling
Whaling attacks are even more targeted, taking aim at senior executives. Although the end goal of whaling is the same as any other kind of phishing attack, the technique tends to be a lot more subtle.
Tricks, such as fake links or malicious URLs, aren’t applied in this instance, as criminals are attempting to imitate other senior staff members.
Whaling emails also commonly use the pretext of a busy CEO who wants an employee to do them a favour, for example:
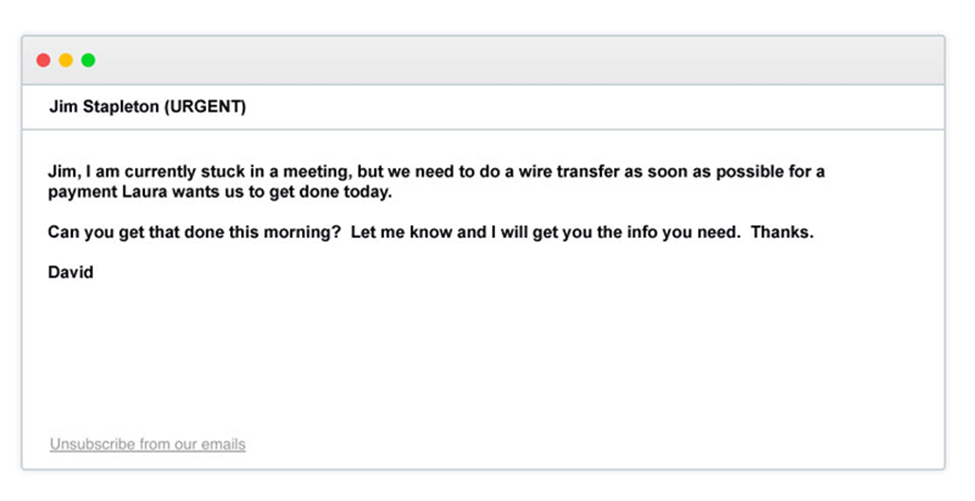
4. Smishing and vishing
With both smishing and vishing, phone calls replace emails as the means of communication.
Smishing involves criminals sending text messages (the content of which is much the same as with email phishing); vishing involves a phony phone call.
One of the most common smishing examples are messages sent supposedly from your bank, alerting you to some suspicious activity:
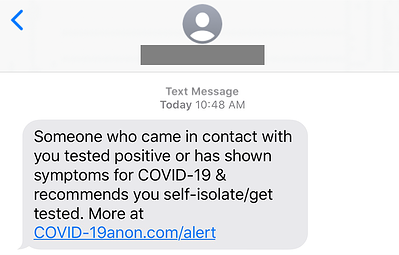
What can you do if you’ve accidentally clicked on the phishing link?
1) Disconnect your device,
2) Back up your files,
3) Scan your system for malware,
4) Change your login credentials.
Employees are the last line of defense
Organizations can mitigate the risk of phishing with technological means, such as spam filters, but these have consistently proved to be unreliable.
Malicious emails will still get through regularly, and when it happens, the only thing preventing your organization from a breach is your employees’ ability to detect their fraudulent nature and react appropriately.
 For more tips and insights on digital security, register to our Digital Safety & Security self-paced course, available for free here:
For more tips and insights on digital security, register to our Digital Safety & Security self-paced course, available for free here:
Liked the article? Would like to take the tips with you?
Here's a downloadable infographic:
 ➡️ You may also wish to check out ➡️ this article on phishing and hacked Social Media account tips produced by NIOK in collaboration with Drive Online Marketing.
➡️ You may also wish to check out ➡️ this article on phishing and hacked Social Media account tips produced by NIOK in collaboration with Drive Online Marketing.
